Information / Flow
What is the threat of security vulnerabilities?
New and more sophisticated vulnerabilities are discovered every day.
Hackers will continue to develop more advanced cyber-attacks to break into corporate networks and steal sensitive data. Mason's security testing team makes effort to keep up with the latest changes in the information security field by constantly monitoring for new vulnerabilities and checking for updates to the scan tool database.
Daily IT operations causes security vulnerabilities due to changes in application and network configurations.
Changes to application and network components can create new security weaknesses.
New vulnerabilities may arise after changes are made to a customer's network or applications. With that in mind, the security team should conduct a vulnerability assessment after each major update or release to ensure that the changes implemented do not open new avenues for intruders to attack your infrastructure.

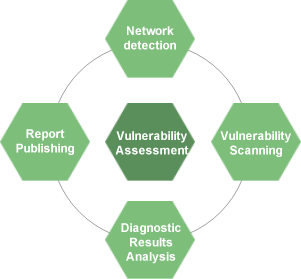
MASON's Security Vulnerability Assessment Services
Mason's Vulnerability Assessment provides diagnostic services for the following IT infrastructure and application vulnerabilities:
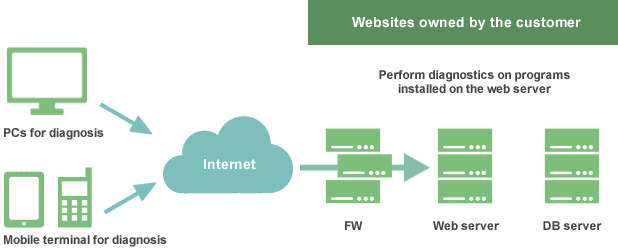
IT Infrastructure Vulnerability Assessment
- Network Vulnerability
- Diagnose operational efficiency of network segments, network access control, remote connection to external networks, implementation of firewall controls, etc.
- Mail Service Vulnerability
- Diagnose susceptibility to phishing attacks and spam emails.
Application Vulnerability Assessment
Diagnose vulnerabilities of web and mobile applications to high-security risk attacks.
Assess how data is stored in apps, how apps transfer information, and if authentication is provided in user desktop applications.
MASON's Vulnerability Assessment Approach
Mason's security team uses a combination of automated and manual approaches to perform vulnerability assessments.
Automated Approach
Automated scanning tools are determined based on customer's needs, requirements, and budget. These scans can detect if customers are exposed to those vulnerabilities because of the database management of vulnerability knowledge. The main advantage of an automated approach is that it provides broad coverage of security weaknesses that may exist on different devices and hosts on the network, regardless of time.
Manual Approach
Manual tuning of scan tools as well as manual validation of scan results to eliminate false positives. Upon completion of these manual assessments performed by our experts, you will receive reliable results that contain only confirmed incidents.
Security Vulnerability Assessment Report
Two reports of the security vulnerability assessment will be delivered to the customer as follows:
- Executive Summary
- Information about the customer’s overall security status and any weaknesses identified in a way that is easy to understand for employees who are not fully knowledgeable in the security field will be provided.
In addition to this, valuable recommendations on corrective actions to be taken to remediate the vulnerabilities revealed will be provided. - Various Diagnostic Results
- The degree of compliance with various security regulations, certifications, and standards (PCI DSS, NIST, GDPR, etc.) will also be included in the report.
Service Contents
| Self-inspection | Simple vulnerability checklist is used to perform a simple diagnosis of 20 major web application vulnerabilities. |
|---|---|
| Simple Diagnosis | Diagnosis is performed using a combination of tools. Comprehensive web application vulnerability assessment is available at a low cost. |
| Standard Plan | Manual diagnosis is performed. Comprehensive and highly accurate Web application vulnerability assessment is possible. In addition to vulnerabilities, proposals for security improvements to further raise the level of security will be provided. |
| PCI DSS Compliance | Web application vulnerability assessments in compliance with PCI DSS requirements is also performed. |
MASON provides services tailored to the customers' needs. Please contact us.
- Inquiries and consultation by phone: +81-3-6425-6735 Business hours 9:00 am - 6:00 pm
- Click here for inquiries, consultation, and estimate request by e-mail.
