Information
What is NIST Security Compliance?
The NIST Cybersecurity Framework is a framework developed by the National Institute of Standards and Technology (NIST) that skillfully leverages the growing complexity and persistence of critical infrastructure systems to improve national security, economic, and citizen safety and health.
Therefore, companies whose security measures are not NIST security compliant may be at risk of not fully meeting the bid criteria.
NIST defines the approach to cybersecurity measures:
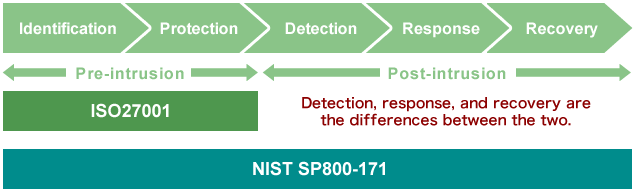
Differences between ISO 27001 (ISMS) and NIST Security Compliance
The major difference between ISO27001 and NIST SP800-171 is the scope of security measures.
ISO 27001 focuses on "prevention" of cyber-attacks and does not adequately cover the identification and the prevention aspects. On the other hand, NIST SP800 covers all aspects like identification, prevention, detection, response, and recovery. Therefore, NIST is the ideal framework for cyber security attacks.
Particular emphasis is placed on detection, response, and recovery after an unauthorized intrusion, which is not included in ISO 27001. In other words, NIST requires post-cyber-attack security measures such as multi-layered system defense which needs supplemental processes compared to ISO27001.
Differences between ISO27001 and NIST:
Impact on Japan
In response to the U.S. government policy, Japan will begin to implement processes at the same level as NIST SP 800-171 for Defense Procurement.
* Refer to September 14th, 2018 for the Acquisition, Technology & Logistics Agency's concept of new procurement standards to be executed in the next fiscal year.
MASON's NIST Security Compliance Services
MASON has a NIST-compliant team available for one-stop consulting in cybersecurity from business risk to system operation. Team members have an extensive consulting experience for ISO27001 certification in addition to consulting experience for NIST compliance.
We can leverage this knowledge to provide NIST security compliance consulting services customized for your company.
MASON's Approach to NIST Security Compliance:
- 1. Identification of critical information assets
-
- Identification of targeted critical information assets
- Identification of lifecycle of critical information assets
- Creation of control ledgers for critical assets
- 2. Risk assessment
-
- NIST Security Compliance Checklist
- Business impact, risk assessment, and analysis
- Documentation of risk assessment criteria
- 3. Internal audit of NIST security compliance
-
- Self-inspection of security measures in all departments
- Conduct internal auditor training
- Conduct internal audits
- 4. Develop and implement a remediation plan
-
- Corrective action plan created
- Corrective action taken
- 5. Progress observation
-
- Confirmation of security operation status
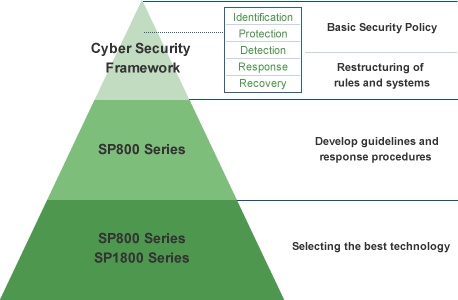
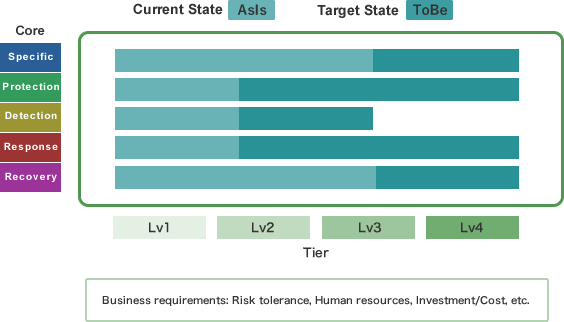
Composition of NIST
NIST consists of three elements: Core, Tier, and Profile, which help companies and organizations analyze the gap between their current and target cybersecurity measures.
| No | Component | Definition |
|---|---|---|
| 1 | Core | List of cyber security measures defined by certain categories |
| 2 | Tiers | Maturity evaluation criteria (4 tiers) to quantify countermeasure status |
| 3 | Profile | As Is (current) and To Be (goals) of the organization's cybersecurity measures |
What is the Core Composition?
The NIST CSF core describes cybersecurity measures that are common to all industries and business types.
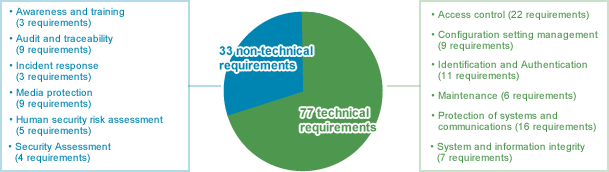
The SF core consists of five functions and 23 categories. For each category, there are subcategories, with a total of 108 subcategories.
Many may be familiar with the five functions of the core, as they are the iconic items of the NIST CSF.
The five are Identify, Protect, Detect, Respond, and Recove
| Function | Identifier | Category |
|---|---|---|
| Identification | ID.AM | Asset Management |
| ID.BE | Business Environment | |
| ID.GV | Governance | |
| ID.RA | Risk Assessment | |
| ID.RM | Risk Assessment Management Strategy | |
| ID.SC | Supply Chain Management | |
| Defense | PR.AC | Access Control |
| PR.AT | Awareness and Training | |
| PR.DS | Data Security | |
| PR.IP | Processes and procedures for safeguarding information | |
| PR.MA | Maintenance | |
| PR.PT | Protection Technology | |
| Detection | DE.AE | Anomalies and Events |
| DE.CM | Ongoing Security Monitoring | |
| DE.DP | Detection Process | |
| Response | RS.RP | Response Plan Development |
| RS.CO | Communication | |
| RS.AN | Analysis | |
| RS.MI | Reduction | |
| RS.IM | Improvement | |
| Recovery | RC.RP | Create recovery plan |
| RC.IM | Improvement | |
| RC.CO | Communication |
The purpose of using the NIST CSF is to maintain and enhance the level of cybersecurity measures. To achieve this, it is essential to align the scale of measurement with the current state (As Is) and the target state (To Be) that we are aiming for.
What is a SOC report?
SOC report stands for "System and Organization Controls.
It is a report used to verify the status of internal controls of an outsourced company.
MASON provides assurance on internal controls for security by issuing a certificate of assurance on internal controls related to security, availability, processing integrity, confidentiality, and privacy (SOC Report).
MASON provides customization of services to suit our customers' needs. Please contact us first.
- Inquiries and consultation by phone: +81-3-6425-6735 Business hours 9:00 am - 6:00 pm
- Click here for inquiries, consultation, and estimate request by e-mail.
